Ethical Hacking Tutorial
Ethical hacking is becoming popular these days because of the increased importance of the data. All sizes of organizations are following ethical hacking practices to secure their most sensitive data and to prevent threats from the black hat hackers. In this Ethical hacking tutorial for beginners and experienced we are going to cover all the fundamental concepts to provide you with complete knowledge. This tutorial helps you in becoming familiar with the concepts like what is hacking, types of hacking, stages of hacking, ethical hacking tools, social engineering, environment setup, phases of ethical hacking, advantages and disadvantages of ethical hacking, etc. Before getting into the tutorial part lets gain knowledge of some basic concepts to understand the tutorial better.

What is Hacking?
Hacking is defined as a process of Identifying the weak points in a network or computer to steal or accessing the private information of organizations and the general public. A simple example of hacking is cracking a password using an algorithm to gain access to a computer. These days computers have become an integral part of every business. Without the computer, there is no business that exists today. The computers need to be networked with an external system and outside partners for making the communication. This makes easy for hackers to enter into the network and steal sensitive information. Hacking means using systems to conduct fraudulent acts such as privacy invasion, fraud, stealing governments, corporates, personal data, etc. Organizations around the world are losing millions of dollars every year. Businesses are taking measures to protect themselves from falling for cyber attacks.
Who is a Hacker?
A hacker is an individual who possesses a skill set of computers, networking, and other talents to find a solution to technical problems. But in general, the term hacker refers to a candidate who uses his or her skills to gain unauthorized access to private networks with an intention to commit crimes. A hacker may hack the system or network for different reasons which include to hurt people via identification theft, bringdown system or hold data to collect a ransom.
History of Hacking
The hacking came to light almost five decades ago and has become a broad discipline. The first hacking was recorded in 1960 at MIT and the word was hacker originated at the same time.
What is Ethical Hacking?
Ethical hacking is also called as a penetration testing in which an ethical hacker uses his skills and ability to test the system. An ethical hacker uses tools and techniques which are used by malicious users with the permission of authority to test the vulnerability or easily affected areas.
Ethical hacking allows an organization to detect the problems before they even get worse. It makes the organization highly secured and frees from falling in the hands of malicious hackers. Ethical hackers have to submit the vulnerabilities they found during testing to the management and are responsible for preparing plans for making a system or network security.
Why is Ethical Hacking is Important?
Data has become one of the most important assets of every organization. So to protect this valuable asset, the best choice for organizations is Ethical hacking. Every organization has some or other valuable information to store and they don’t want to reveal it for outsiders. Whether it is a government or private organization it has to interact with various web applications over the internet on a daily basis to run their business. There are many chances where attackers find your network vulnerabilities through your interactions and commit cyber attacks.
The present hackers are smart and intelligent in their own way when it comes to penetrating the system. Recent security breaches have cost millions of dollars across the world. This has brought a big impact on data security. Organizations have started hiring ethical hackers to identify the vulnerable areas and to protect them from cybercriminals.
What is meant by a security threat?
An ethical hacker needs to deal with a bunch of security threats on a regular basis. Any type of risk that has the potential to damage the system or organizations as a whole is called a security threat. There are two types of threats that are physical and nonphysical.
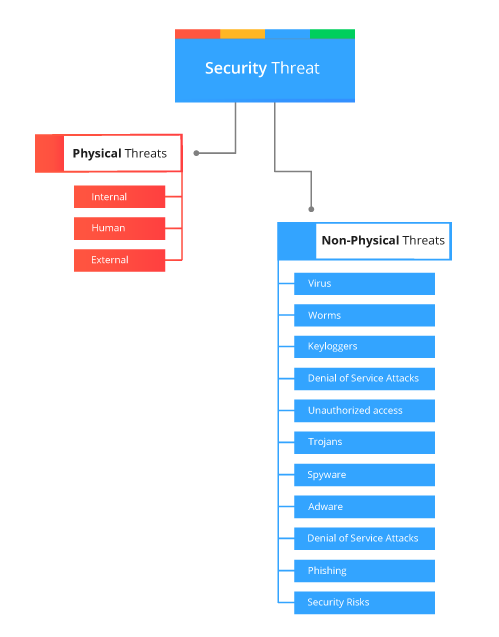
Physical Threats
The physical threat is nothing but someone stealing a computer system that has valuable data. Physical threats are further divided into three categories.
- Internal e.g. faulty power supply, hardware fire, internal hardware failovers, etc
- Human e.g. vandalism, accidental errors, arson, etc
- External e.g. floods, earthquakes, fires, etc
Non-Physical Threats
The non-physical threat is something in which the attacks have to arises in the form of the virus. These threats are also termed as logical threats. The below-mentioned list is the common types of non-physical threats;
- Virus
- Worms
- Keyloggers
- Denial of Service Attacks
- Unauthorized access to computer data
- Trojans
- Spyware
- Adware
- Distributed Denial of Service Attacks
- Phishing
- Other Computer Security Risks
Following strategies would help you in protecting your data from the above threats;
- To protect from viruses, worms, Trojans, etc you need to install anti-virus software. In addition to antivirus, you need to have some control measures on the use of external storage systems and unauthorized programs downloading onto the computer.
- Using strong authentication methods can prevent unauthorized users from accessing the data. The authentication strategies should be in the form of Smartcards, User Ids, strong passwords or Biometric, etc.
- Using Intrusion-detection/prevention strategies can help to protect from denial of service attacks.
Types of Hacking

The hacking has been segregated into different types based on what is being hacked. Below mentioned are the various types of hacking examples.
- Website Hacking: this means unauthorized controlling over a web server, its databases and other interfaces of a website.
- Network Hacking: Network hacking is a method to collect information about the network by using different tools like Ping, Telnet, Tracert, NS lookup, Netstat, etc. This is mainly performed by malicious hackers with an intent to create harm to the network system and hamper its operations.
- Email Hacking: It means accessing the emails of others in an illegal way or without the consent of its owner.
- Ethical Hacking: This involves a process of testing vulnerable areas in a system or network for cyber attacks and fixing them with the consent of an authorized person.
- Password Hacking: it is a method to recover secret passwords that are encrypted and stored in a computer system.
- Computer Hacking: it is an act of stealing computer passwords and ID by using hacking methods and accessing a computer in an illegal way.
Advantages of Hacking:
Hacking is beneficial in the below scenarios:
- To get back the lost information
- To conduct penetration testing to strengthen the network security
- To take advance measures from falling for cyber attacks.
- To make plans for preventing attackers.
Disadvantages of Hacking:
Hacking can cause huge damage when it is done with the wrong intent, it can cause:
- A big security breach
- Illegal access to confidential & private information
- Hampering system operation
- Privacy violation
- Malicious attacks
- Denial of service attacks
Types of Hackers
Hackers are mainly categorized into three major categories which include a white hat, black hat, and grey hat. The hackers have divided into different categories based on their intent to hack something. These terms have come from the old Spaghetti Westerns, in which the bad guy wears a black hat and the good one wears a white hat.
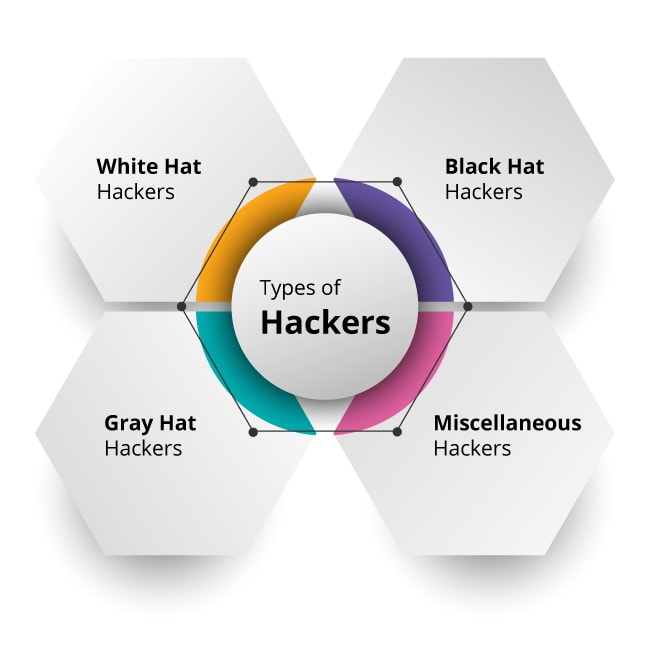
White Hat Hackers
These hackers are also called as Ethical hackers. They are quite opposite to the black hat hackers. These guys’ intention is not to harm the system or network but to find the weak areas in a system or network and fix them in advance.
Organizations across the world are using Ethical hacking to protect their data and Ethical hackers have high demand in the market. A wide range of opportunities is available for skilled Ethical hackers.
Black Hat Hackers
These are the hackers whose intention is to access the data in an illegal way with a wrong intention. Black hat hackers hack the sensitive information of organizations and harm its operations.
Black Hat hacking is always considered as an illegal activity because it is done with an intention to steal the corporate data, damaging the system, violating the privacy, blocking network communication network, etc. It is considered as a crime and legal action shall be taken against the culprits.
Gray Hat Hackers
Gray hat hackers are a combination of both white hat and Blck hat hackers. These are the people whose intention is not to cause any harm or danger to the system or network but they exploit a computer system or network without the consent of the owner.
Their intent is to bring the vulnerable areas into the notice of the owner with anticipation of appreciation or little bounty.
Miscellaneous Hackers
Apart from the above-mentioned Hackers, there are few other hackers as well. They are divided based on the intention and their level of expertise in hacking. They are:
- Red Hat Hackers
- Blue Hat Hackers
- Elite Hackers
- Script Kiddie
- Neophyte
- Hacktivist
Ethical Hacking Skills
An Ethical hacker is a computer expert who specializes in finding and protecting networks and systems from being falling in the hands of hackers. Like any other expertise, you are required to acquire complete knowledge to become an expert Ethical hacker. Once you are on the track you need to keep yourself updated with the latest technologies and advanced vulnerabilities.
Following are the list of skills one should possess.
- One should gain expertise in different operating systems, and the first one to consider is Linux and it’s distribution. This is because a majority of the vulnerability testing includes sifting through systems and invading the target systems. It is an impossible task to execute without good command over the operating system.
- Networking expertise is a great advantage for an ethical hacking career. Ethical hacking is associated with Packet sniffing, packet tracking, scanning subnets detection & prevention, etc.
- Programming expertise: As an ethical hacker you are not required to be an expert in all the languages but you should be a jack-of-all-trades.
Below mentioned are the majorly used programming languages in Ethical Hacking for different purposes.
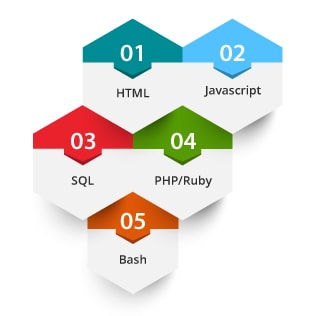
- HTML: This language is mainly used for creating web pages. The HTML forms allow the user to enter the data all over the internet. The ability or skill to construct your own forms will help you in examining the vulnerabilities and in finding the weak points in the code.
- Javascript: It is a client-side scripting language and also helpful in writing backend code. It is executed on the client browser and having the knowledge of JS can help the ethical hacker in analyzing the cookies, executing cross-site scripting, etc.
- SQL: The Structured Query Language (SQL) is used for interacting with databases. Knowledge of SQL will allow you to identify the web application algorithms that are weak and you can delete data from those databases etc.
- PHP/Ruby: It is a server-side scripting language. PHP is a widely-used programming language for website development. It allows you to make customizations and process HTML forms. You can write a custom application in PHP for modifying the setting on a web server and make servers free from vulnerable attacks.
- Bash: This is used for creating handy scripts and small batch files. It helps at times when you are required to write your own shellcodes, rootkits, exploits, or understanding existing ones.
Popular Ethical Hacking Tools:
There are various Ethical hacking tools available but, here we are going to discuss the popular Ethical hacking tools used by Ethical hackers.
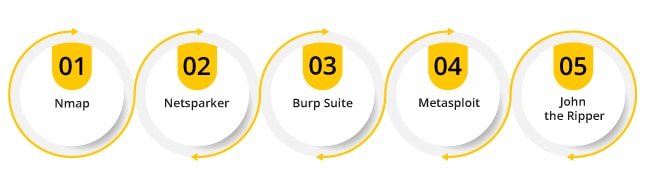
Nmap
Nmap is a short form of Network Mapper, it is a free and open-source network scanner developed by Gordon Lyon. Nmap helps Ethical hackers in gathering information about a target system. This information is very vital for planning the steps to attack the target system. Nmap allows Ethical hackers in finding the hosts and services on a computer network by way of sending Packets and examining the responses. Nmap is capable enough to work on cross-functional platforms such as Windows, Mac, and Linux. It has become a popular tool in the hacking segment due to its fast scanning and powerful searching abilities.
Netsparker
Netsparker is an automated web security scanning tool. This tool allows ethical hackers to scan websites, web services, and web applications and finds security flaws. It is designed in a highly flexible way to scan all web applications irrespective of the technology on which they are built. It’s highly reliable scanning services not only finds the vulnerabilities but also eliminate the recheck work by providing dead proof results.
Netsparker is the only security scanner that is capable of making automatic exploiting to identify vulnerabilities in a read-only safe way. It also makes your work hustle free by providing proof.
Burp Suite
It’s a Java-based web Penetration testing framework. It has become a popular tool accepted by the majority of industry Information security professionals. It simplifies the process for ethical hackers in identifying the vulnerable points in a network and verifies the attack vectors that cause damage to the network.
Burp Suite has become a highly acceptable tool because of its capabilities. It can map content and functionality very accurately, Automatically handles sessions, manages the changes like volatile content, and application logs.
Metasploit
The Metasploit is an open-source tool widely used by Ethical hackers as well as cybercriminals to probe the weak points in servers and networks. It was written in Ruby and allows the network administrator to hack his own network to find the vulnerable points and security risks. It acts as the best tool for beginners to master hacking skills. Metasploit allows you to replicate for social engineering and phishing purposes.
As Metasploit is an open-source tool making customizations are very easy with it and used with most operating systems. Once the flaws are identified and documented the same information can be used for fixing the weakness and prioritize solutions.
John the Ripper
It is one of the most popular tools used for cracking passwords. And the best available option to check the strength of a passcode in your operating system, or for auditing the remote systems. This is highly advanced and auto-detects the type of encryption used in almost any type of password and makes a modification to a password test algorithm appropriately. These are the things that have contributed to making it a most intelligent toll for cracking the passwords.
What is Social Engineering?
Social engineering is an effective mode of hacking among all other malicious activities. It is a way to collect information from the users with the wrong intentions. In which psychological manipulations are used to trap or guide users into making security mistakes or persuading them to share sensitive information.
The social engineering involves a sequence of steps and proper planning before it actually starts. A perpetrator first studies the intended victim to collect the required background details, such as appropriate points to entry, weak protocols, etc. Then, the attacker starts persuading the victim and stimulate the victim to take the actions that break security practices which include gathering access to sensitive data or revealing critical resources.
Social engineering techniques:
Here are the different methods used for social engineering. Let us discuss them in detail.
Familiarity Exploit
It is one of the familiar methods used in social engineering. You will respond to the people quickly whom you are familiar with. can’t you? Yes right. In the same fashion, the preparator gets familiar with the targeted person and becomes friendly.to make this possible. A preparator will perform different things which include, going out for drinks, joining someone for smoke, playing video games, creating similar habits, etc.
Phishing
It is also one of the widely used social engineering methodologies. It involves developing counterfeit websites that look similar to the real ones. People who visit these malicious sites believe that they are real ones and submits sensitive data and passwords. The user-submitted data is automatically redirected to the hacker’s system.
Exploiting Human Emotions
One can simply fall for human emotions and this has become the best option for the perpetrators to conduct social engineering. Feelings such as pity and greed are very quickly triggered. A Social engineer intentionally drops a virus in the targeted area where a user can easily trap for it. The user is most likely to plug that disk into their system. The drive may be infested with all types of nonphysical threats.
Phases of Ethical Hacking
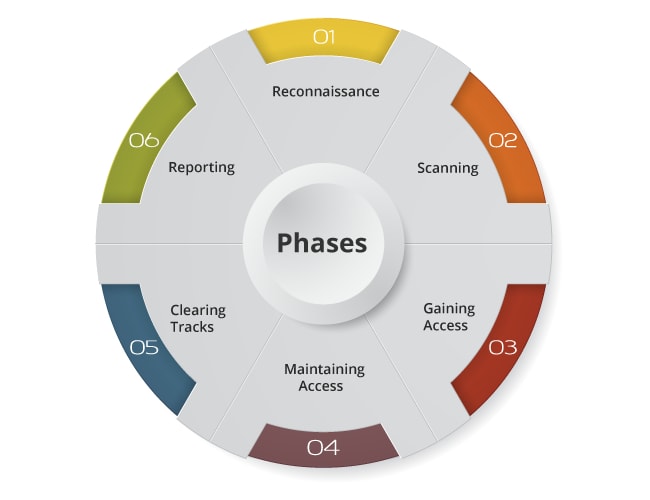
Like many other projects, ethical hacking also goes through various phases. It allows Ethical hacker to make a structured ethical hacking attack.
There are majorly six different phases followed by the majority of the Ethical hackers which are:
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Clearing Tracks
- Reporting
Reconnaissance
It is the phase where the attacker collects all the possible information of the target in a passive or active means. To complete this process attackers follow some tools which include, NMAP, Maltego, Hping, and Google Dorks.
Scanning
This process involves a keen investigation. The scanning process helps the attacker to analyze the target network or machine to look for vulnerabilities that can be exploited. Attackers follow different tools which include Nexpose, Nessus, and NMAP.
Gaining Access
Here in this phase, the vulnerability area is located and the attempt will be done to exploit the network. The tool used for gaining access is Metasploit.
Maintaining Access
This is the phase where the hackers have already gained access to the targeted system. The hacker will install some backdoors in the targeted system so that he can easily access the system in the future. To do this Metasploit is the widely used tool.
Clearing Tracks
This is considered an unethical activity because one has to remove all the log activities that had taken place during the hacking process.
Reporting:
This is the documentation and submitting process where the Ethical hacker records the complete process in it. The report contains things like findings, tools used, success rate, exploitation process, and vulnerabilities found.
Ethical Hacking Environment Setup
Here we are going to discuss the complete information on how to perform ethical hacking. To perform the ethical hacking we need a Kali Linux operating system. We have the option to download the Kali Linux OS in a virtual box. Below mentioned are the simple steps to download the virtual box and Kali Linux.
Step 1: Download Virtual Box:
In the very first step, we download the virtual box because it helps us to create a virtual machine on your present operating system. Once we are done with the installation process of the Virtual box, we will download the Kali Linux. A virtual machine is just like another machine. The operating system will work just like installed on a separate laptop. Using the below link you can download the operating system and install it.
https://www.virtualbox.org/wiki/Downloads
Once you are done with the installation process the virtual box will appear like below.
Step 2: Downloading the Kali Linux:
Here we are going to download Kali. It comes with the applications and programs that are preconfigured and pre-installed. Once you are done with the installation you can use it for hacking.
In two ways you can install kali. Either you can install Kali in your present operating system, or you can download and utilize it as a core operating system. Here, we will be using a virtual machine in this tutorial.
Click on the below link to download the Kali Linux.
https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/
You are now required to click on Kali Virtualbox Images to get that download.
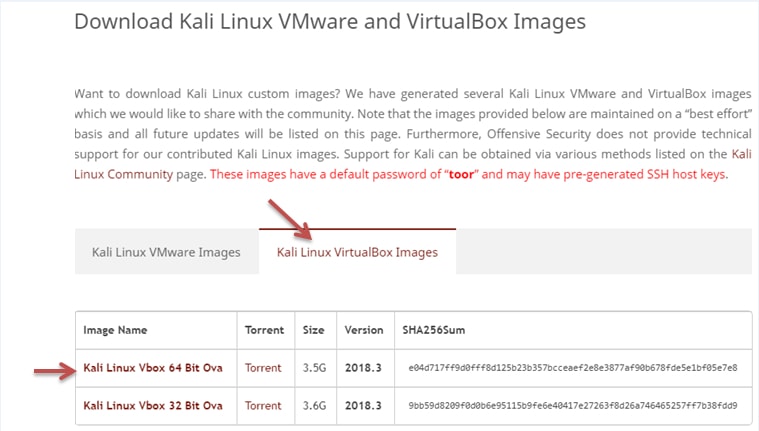
- The best option is to go for a 64-bit version if your computer is 64 bits otherwise, go for the 32-bit version.
- The file you are going to download must contain the .ova extension, if the file does not contain this extension then you have downloaded the wrong one.
After it gets downloaded with the .ova extent you need to double click on the file and click on the import button.
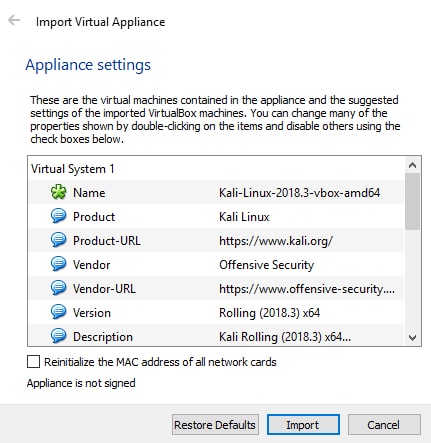
Once you are done with the installation process the Kali Linux will look like below
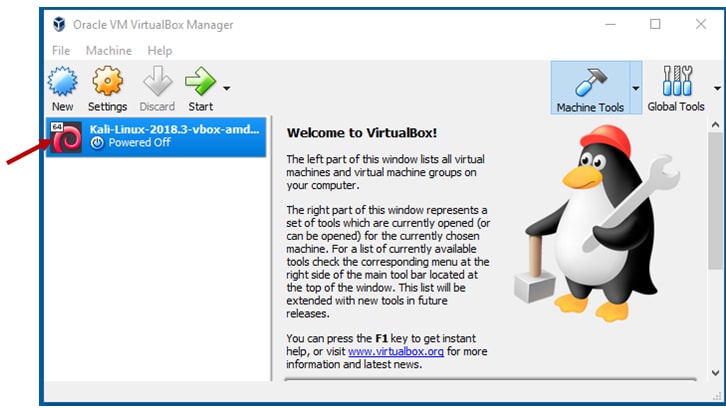
Step 3: Modify some settings of Kali Linux
Here we are required to make some modifications. To make changes click on the Kali Linux on the left side and go to settings. Now click on system and change the amount of RAM based on the existing RAM on your computer. If you wish to give it as 2 GB you can, but one GB is ideal for kali.
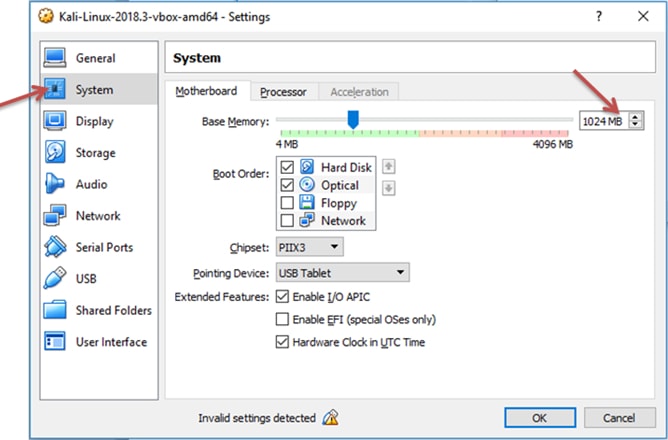
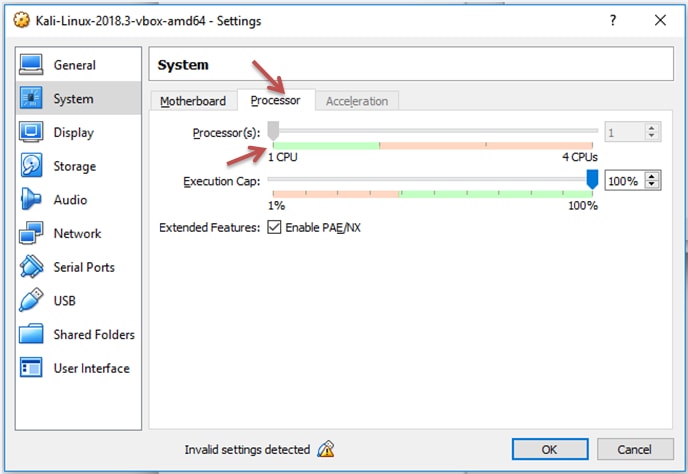
If you want to modify the processor amount you need to click on Processor. 1 CPU is enough for Kali.
Now click on Network settings and set “ Attached to “as “NAT Network”. Sometimes the network is created automatically by the virtual box, sometimes it may not. If the Network is automatically created then click on OK. If the Network is not created then you will be displayed with the image like below.
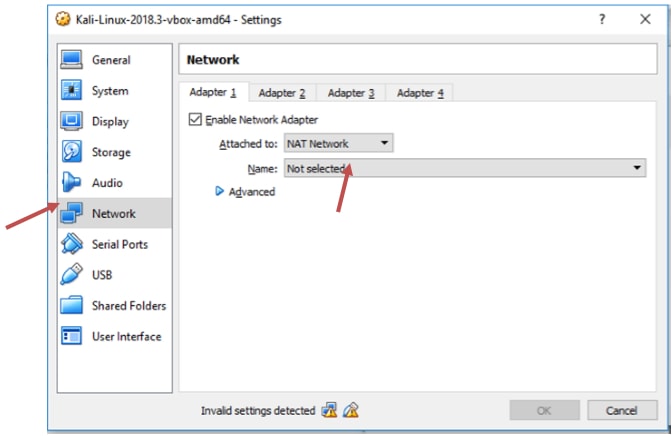
If you find that the virtual box is not created the network automatically, then you are required to go to the VirtualBox → Preferences → Network → + sign. Now it creates another network.
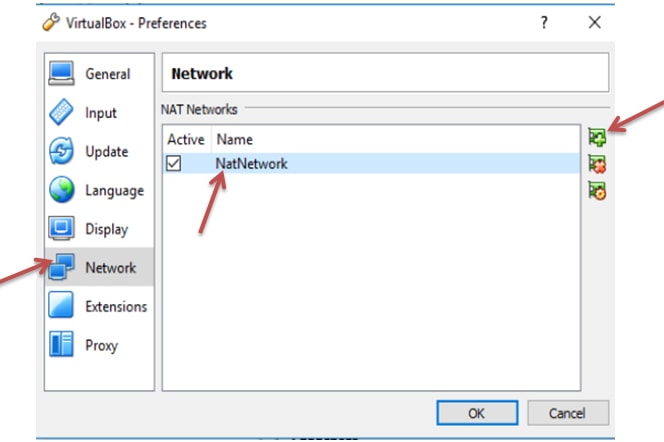
Step 4: Starting of Kali Linux
Now it is the time for starting the Linux Kali by hitting the start button. Once you click on the start two cases will arise:
- Start successfully
- Arises error like this:
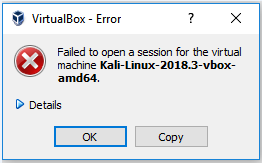
To fix the above error, you need to download the Oracle VM Virtualbox box which should be the same version of VirtualBox.
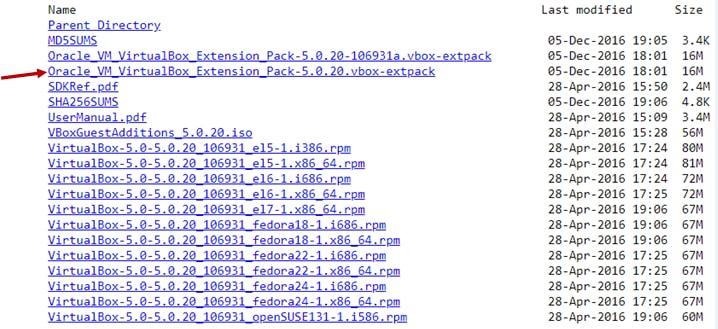
Now click on Oracle_VM_VirtualBox_Extension_Pack-5.0.20.vbox-extpack and download it.
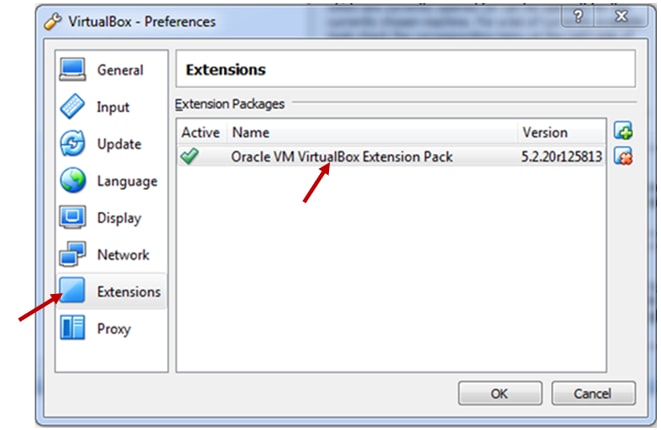
When you are done with installing, to check the download click on File → Preferences → Extensions. Here you will find the Oracle VM VirtualBox extension pack. Click on Ok.
All the problems have been fixed so far, it is the time to start the virtual machine by clicking on the start button.
After starting, you will be asked for the Username, and the default Username is root then you are asked to provide the password and the default password would be reverse of the root which is toor. Now the screen appears as shown below.
Conclusion:
So with this, we have come to the end of this ethical hacking tutorial, I hope you have gained the complete overview of different concepts and tools associated with ethical hacking. If you are aspiring to start your career in ethical hacking, it is a good time to start and it is advisable to go for formal training to become an expert. Happy learning!
